If you were hoping to splash your Bitcoin on luxury real estate in Dubai, you may have to wait a little longer.

According to The Times , the world’s first luxury development to be sold using the cryptocurrency is on hold.
The Aston Plaza development in Dubai was promoted by Baroness Mone, a controversial lingerie mogul whose past business ventures have been called into question .
Mone launched the $323 million (£250 million) project in September 2017 alongside her billionaire partner Doug Barrowman. At the time, marketing materials said the two residential towers would be finished by summer 2019.
The development, where a two-bedroom flat would set you back approximately $240,000 (£185,000) in Bitcoin, is described on its website as being 25 percent done.
But, according to government inspectors who visited the site in January last year, the venture is on hold, and construction has seemingly ceased.
Mone has been involved in the cryptocurrency industry for some time. She founded Equi Capital, which issued an Ethereum-based token to allegedly make investing more accessible. Apple co-founder Steve Wozniak was working directly with the project.
As previously reported by Hard Fork , Mone’s Equi project was originally set for launch as an initial coin offering (ICO), but failed after a short pre-sale.
It initially raised $7 million through private token sales, but by the time it was set to go public, interest lessened and targets were missed. The ICO was cancelled and refunds were issued to investors.
To make up for the missed fundraising opportunity, the company launched a marketing bounty program which would issue public tokens to advertise Equi. The marketing firm running the program cut all ties with Equi soon after launch. Participants in the bounty said they had missed out on lucrative rewards promised by Equi Capital.
Did you know? Hard Fork has its own stage at TNW2019 , our tech conference in Amsterdam. Check it out .
Hackers target major UK supermarket’s Twitter with phoney Bill Gates Bitcoin scam
Hackers took control of British multinational retailer Tesco’s Twitter account yesterday, urging followers to send Bitcoin to a wallet address and promising to return twice the value received.
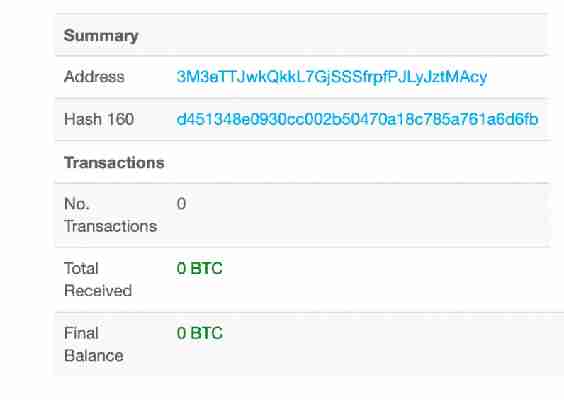
Luckily, though, Tesco’s followers did not fall for the Bitcoin scheme as no funds were deposited in the wallet address shared by the hackers.

According to Bleeping Computer , the tweet was sent from Tesco’s official account, which boasts over 500,000 followers.
Hackers also decided to retweet and impersonate Bill Gates, changing the supermarket’s Twitter handle to @Billgatesmsc, and replacing the account’s original profile picture to that of the tech magnate. All the changes resulted in Tesco briefly losing its verified status, prompting the supermarket’s followers to speculate something was amiss.
The hacker also took the chance to reply to complaints from Tesco customers, requesting their full names, addresses, and postcodes in a seeming attempt to solve their queries.
At the time of writing, Tesco had regained control over its Twitter account and all unauthorized tweets have been deleted.
Tesco is yet to provide full details on how the attackers were able to gain control of its Twitter account, but Hard Fork has reached out and will update this story if we hear back.
Although in this instance the hackers failed to get the funds, it’s not the first time they try their luck by taking control of Twitter profiles, often at a brand’s or organization’s expense.
Back in April, malicious actors defaced the Twitter account of Sweden’s governing party with hate speech. They also said they would replace the Swedish krona with Bitcoin.
Prior to that, in November last year, hackers hijacked a host of verified Twitter accounts to promote fake cryptocurrency giveaway links, this time using Elon Musk‘s name.
The same month, Pathé’s – the world’s second oldest operating film company – Twitter account was hacked to promote yet another Elon Musk cryptocurrency scam.
US hospitals opt for paying hackers to survive Ryuk ransomware attack
Cybercriminals are targeting hospitals across the globe with ransomware. Some of the hospitals are giving in to the attackers’ demands and paying the requested ransom, likely in cryptocurrency.

Over in the US , Alabama-based DCH Health System said it paid the hackers after the attack severely disrupted operations at three hospitals, the Tuscaloosa News reports .
Specifically, computers at the DCH Regional Medical Center in Tuscaloosa, Fayette Medical Center, and Northport Medical Center were infected from October 1 onwards. DCH Health System said there was no indication that patients records had been compromised.
It comes after the Federal Bureau of Investigation (FBI) issued a warning highlighting that the number of sophisticated attacks on businesses and state and local government, was on the rise.
Although no group has claimed responsibility, it’s being reported that Ryuk , which the UK ‘s National Cyber Security Centre previously said could become a global threat , is the specific ransomware variant behind the attacks .
Security firm Crowdstrike says evidence suggests Ryuk attacks may be coordinated by a criminal group in Russia operating as Wizard Spider, which as of January this year had managed to net $3.7 million worth of Bitcoin.
Worryingly, FBI Flash said in May that cybercriminals had targeted over 100 US and international businesses with Ryuk ransomware since August 2018.
Indeed, the spread of the ransomware seems to have become a global issue. Over in Australia , seven hospitals in Gippsland and south-west Victoria, have also reported ransomware infections.
The ransomware attack caused the hospitals to disconnect multiple computer systems, meaning that some patient records, booking, and management services were offline.
Just last week, Hard Fork reported on how a hacker was holding computer systems in the southern Spanish city of Jerez de la Frontera to ransom .
The attack , which reportedly began last Tuesday, had at the time already caused service outages for the city’s website.
How does Ryuk work?
Put simply, Ryuk is a Trojan virus that encrypts files on a compromised computer and then demands payment , typically in Bitcoin , to decrypt them.
Generally speaking, the ransomware is used to target large organizations , with significant annual revenue , in hope of getting larger ransoms from the victims.
Back in April, ransomware support firm Coveware’s report said cryptocurrency payments made to attackers had increased almost 90 percent in Q1 2019 over the previous quarter – an increase largely attributed to Ryuk , which typically demanded around $288,000 per attack .
Want more Hard Fork? Join us in Amsterdam on October 15-17 to discuss blockchain and cryptocurrency with leading experts.











